SMAD LOCK BRANKAS FREE DOWNLOAD
We need to encrypt the file through relative software, example: Flash drive is easy to carry and we use and share data easily in day to day life but its security is also important and necessary. If you have windows 10 Education, Pro, Enterprises edition then enable your write protection with group policy editor. Now you need to choose which encryption mode to use, select compatible mode and click Next. Well, there is a simple answer: How we can encrypt our data through hardware encryption Hardware encryption is a very effective and more secure method of encryption. 
| Uploader: | Nagal |
| Date Added: | 12 April 2007 |
| File Size: | 30.54 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 1290 |
| Price: | Free* [*Free Regsitration Required] |
Select enableclick on Apply and then OK. Now in llock next screen, you need to move your mouse pointer randomly within the window. Actually, here it is happening that, veracrypt collect your mouse pointer randomness for increasing cryptographic strength of encryption key.
Rename the new key folder to StorageDevicePolicies and press enter.
Encrypt USB through Registry editor 2. So, tell us which security steps or which way you use for USB protection brankaw comment. At last click on start encryption to finish this process.

It creates many security features in Windows 10 which are very helpful in terms of our USB securityComputer security, different types of network security etc. How to encrypt data in the USB Drive There are many ways to encrypt your data in the flash drive but I will give you best methods only which work great.
In the next screen select any drive you want. After selecting your volume size click Next. As we all know, sometimes we have more sensitive data and we do not want to show them to other due to some reasons. Non-system partition option, encrypt internal and external drive optionally and create a hidden volume Encrypt the system partition option, encrypt your entire system drive where your windows install so if anyone start your windows it ask for password before windows boot and optionally create a hidden system.
Well, there is a simple answer: Now, select file where you wish to create veracrypt volume container.
The Dukes of Surf
Click on NEXT 8. Detail guide about computer OS Operating System Today I will talk about some features of Windows 10 and software which really helpful for our USB security and it not only valid for windows 10 it also be applicable to another version of windows.
Restart your computer to complete the process. The above method of write protect USB can be applicable only on the computer which enables the write protection registry.

Select first step standard veracrypt volume and click on Next. Encrypt the pock partition option, encrypt your entire system drive where your windows install so if anyone start your windows it ask for password before windows boot and optionally create a hidden system. Now you need to choose which encryption mode to use, select compatible mode and click Next.
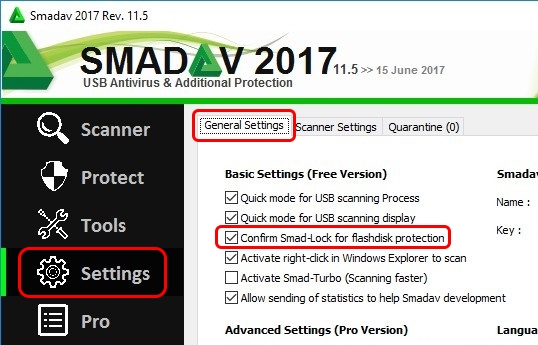
MACHINE: The use Folder SmadAV (Δ Smad-Lock (Brankas SmadAV) Δ)
Now it takes time according to the size of your volume you enter before. I am a computer troubleshooter and solve problem-related to Windows, Android and other tech platforms. After completing click on OK button then Exit. Select your backup option as your convenience and click Smd.
Then, click on Next 8. I also talk about before, in my previous post best software for windows. If you want, select the second option for a hidden volume. If you have windows 10 Education, Pro, Enterprises edition then enable your write protection with group policy editor.
Smad Lock Folder Some People, Some Other Place.epub
After that, enter a strong brankass and click on NEXT. I tried to explain different methods of USB protection that everyone should know. All the methods I mentioned earlier are also very good but some flash drive like IronKey which provide best flash drive hardware encryption, not cheap but work effectively, when you purchase these type of USB smac sure it uses AES bit or FIPS algorithm to encrypt data.
We know that if our attention seems elsewhere, then our data may be stolen by somebody and the same way Malware and Viruses are also one reason to steal and corrupt our data.
Production
Encrypt USB through Third party software 1. Non-system partition option, encrypt internal and external drive optionally and create a hidden volume. Browse the following path:

Комментарии
Отправить комментарий